TCP/IP Model: Routing and Routing Protocols in Network Layer
To properly learn something, we have to start at the beginning. We will be learning one concept at a time, process it, and move to the next.
The goal is consistent learning and absorbing information while feeling engaged and not overwhelmed.
I have divided the network layer articles into six parts.
- Introduction to Network layer
- Addressing in Network layer
- Decoupling the Router
- Routing and Routing Protocols in Network Layer
- Internet Protocol
- DHCP and NAT in Network layer
Goal of this article
I will be discussing the routing and routing protocols in the network layer of the TCP/IP Five-layer network model.
In the previous article, I have talked about the internal working of a Router. Routers try to pick the shortest possible path every time to ensure timely delivery of data. We have to keep in mind that the shortest possible path to a destination network could change over time, sometimes rapidly, intermediary routers could go down, disconnection of links, new routers on the link, and traffic congestion could cause specific routes to become too slow to use.
We'll get to know how routers know the shortest path or path, in general, to deliver a packet from a source to the destination. I will cover the basics of routing and routing tables.
Routing
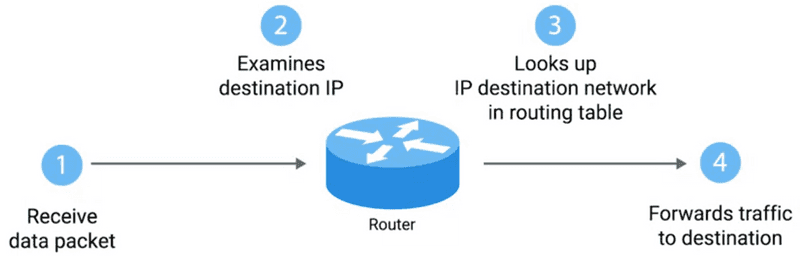
Routing has just a few steps:
-
These steps are repeated as often as needed until the traffic reaches its destination.
-
Routers inspect the destination IP, look at the routing table to determine which path is the quickest, and forward the packet along the path. Looking over of quickest path happens over and over.
Routing Tables
The most basic routing table will have four columns.
-
Destination network
- This column would contain a row for each network that the router knows.
- This is just the definition of the remote network, a network ID, and the netmask.
- These could be stored in one column inside a notation, or the network ID and netmask might be in a separate column.
- When the router receives an incoming packet, it examines the destination IP address and determines the packet's belonging network.
-
Catchall entry
- It matches any IP address for which it doesn't have an explicit network listing.
-
Next hop
- This is the next router's IP address that should receive data intended for the destination networking question. It could just state the network is directly connected and that there aren't any additional hops needed.
-
Total hops
- This is the crucial part of understanding routing and how routing tables work on any complex network like the Internet.
- There will be lots of different paths to get from point A to point B. Routers try to pick the shortest possible path at all times to ensure timely delivery of data.
Routing Protocols
The real magic of routing is that routing tables are always updated with new information about the quickest path to destination networks.
Routers use routing protocols to learn about the world around them. The routers use unique protocols to speak to each other to share what information they might have. Protocols help the router on one side of the planet learn about the best path to a network on the other side of the planet.
Routing protocols fall into two main categories.
-
Interior gateway protocols
-
Link state routing
- Open Shortest Path First Protocol (OSPF)
-
Distance-vector routing
- Routing Information Protocol (RIP)
- Enhanced Interior Gateway Routing Protocol (EIGRP)
-
-
Exterior gateway protocols
- Border Gateway Protocol (BGP)
Interior Gateway Protocols
Routers use interior gateway protocols to share information within a single autonomous system. In networking terms, an autonomous system is a collection of networks that all fall under a single network operator's control. An autonomous system contains routers that share standard traffic policies and administration and is managed by a single organization.
Interior Gateway Protocols can be divided into two categories:
Distance Vector Routing Protocol
-
It uses the Bellman-Ford algorithm for exchanging routing information.
-
Routers using distance vector routing protocols do not possess the topological information about the network but instead rely on the neighbor's information.
-
Information kept by distance vector router:
- Each router has an ID
- Intermediate hops
- Associated with each link connected to a router, there is a link cost (static or dynamic)
- Each router maintains a distance-vector table containing the distance between itself and all possible destination nodes
- Distance to itself = 0
- Distance to all other routers = infinity number
-
The algorithm follow these three steps:
- A router transmits its distance vector to each of its neighbors in a routing packet.
- Each router receives and saves the most recently received distance vector from each of its neighbors.
- A router recalculates its distance vector when:
- It receives a distance vector from a neighbor containing different information than before.
- It discovers that a link to a neighbor has gone down.
-
Routing Information Protocol (RIP)
- It uses hop count as a routing metric to find the best path between the source and the destination network.
- Features
- Updates of the network are exchanged periodically.
- Updates (routing information) are always broadcast.
- Full routing tables are sent in updates.
- Routers always trust routing information received from neighbor routers.
-
Advantage
- It is simpler to configure and maintain than link-state routing.
-
Disadvantages
- It is slower to converge than the link state.
- It is at risk from the count-to-infinity problem.
- It creates more traffic than link-state since a hop count change must be propagated to all routers and processed on each router.
- Hop count updates occur periodically, even if there are no network topology changes, so bandwidth-wasting broadcasts still occur.
- For more extensive networks, distance vector routing results in larger routing tables than link-state since each router must know about all other routers, leading to congestion on WAN links.
Link State Routing Protocol
-
In this protocol, the router posses complete topological information about the network and based on this information, each router independently calculates and builds the routing table.
-
Each router can compute its routing table by using the shortest path computation.
-
Open Shortest Path First Protocol
-
OSPF routing is widely used for intra-AS(Autonomous System) routing on the Internet.
-
OSPF uses flooding of link-state information and Dijkstra's least-cost path algorithm.
-
Each router then locally runs Dijkstra's shortest-path algorithm to determine a shortest-path tree to all subnets, with itself as the root node.
-
OSPF does not mandate a policy for how link weights are set (that is the job of the network administrator) but instead provides the mechanisms (protocol) for determining least-cost path routing for the given set of link weights.
-
A router broadcasts routing information to all other routers in the autonomous system, not just its neighboring routers.
-
The periodic updating of link state advertisements adds robustness to the link state algorithm.
-
OSPF advertisements are contained in OSPF messages carried directly by IP, with an upper-layer protocol of 89 for OSPF. Thus, the OSPF protocol must itself implement functionality such as reliable message transfer and link-state broadcast.
-
The OSPF protocol also checks that links are operational (via a HELLO message sent to an attached neighbor) and allows an OSPF router to obtain a neighboring router's database of network-wide link states.
-
Features:
- Exchanges between OSPF routers (for example, link-state updates) can be authenticated using simple and MD5 authentication.
- When multiple paths to a destination have the same cost, OSPF allows multiple paths to be used (that is, a single path is not a compulsion for carrying all traffic when multiple equal-cost paths exist).
- Integrated support for unicast and multicast routing
- Supports for hierarchy within a single AS with the help of backbone area, area border router, and destination area.
-
Exterior Gateway Protocols
An Exterior Gateway Protocol is a routing protocol that is used to exchange routing information between autonomous systems. Since an inter-AS routing protocol involves coordination among multiple ASs, communicating ASs must run the same inter-AS routing protocol. On the Internet, all ASs run the same inter-AS routing protocol, called the Border Gateway Protocol.
- Border Gateway Protocol (BGP)
- BGP is a decentralized and asynchronous protocol.
- BGP does not have its transport mechanism. Thus BGP uses the Transmission Control Protocol (TCP) for exchanging routing information.
- A BGP connection that spans two ASs is called an external BGP (eBGP) connection.
- A BGP session between routers in the same AS is called an internal BGP (iBGP) connection.
- Terminology
- Route - When a router advertises a prefix across a BGP connection, it includes with the prefix several BGP attributes.
- AS-PATH - The AS-PATH attribute contains the list of ASs through which the advertisement has passed.
- NEXT-HOP - It is the IP address of the router interface that begins the AS-PATH.
- Steps in adding outside-AS destination in a router's forwarding table:
- Learn from the inter-AS protocol that subnet is reachable via multiple gateways
- Use routing info from intra-AS protocol to determine costs of the least-cost paths to each of multiple gateways.
- Hot potato routing - choose the gateway that has the smallest least cost.
- Determine from the forwarding table the interface leads top least-cost gateways and enter it in the forwarding table.
Did you find this post useful?
I would be grateful if you let me know by sharing it on Twitter!
Follow me @ParthS0007 for more tech and blogging content :)
Newsletter
If you liked this post, sign up to get updates in your email when I write something new! No spam ever.
Subscribe to the Newsletter